fail...MainActivity.java
String textData = "b2FueHVl";
...
String roysue_1 = Test.hallbBase64(MainActivity.this.username_et.getText().toString());
if (roysue_1.compareTo(MainActivity.this.textData) == 0) {
Toast.makeText(MainActivity.this.getApplicationContext(), "sucess.....", 0).show();
} else {
Toast.makeText(MainActivity.this.getApplicationContext(), "fail.....", 0).show();
}
...
复制在这里注册了native方法
Test.java
public class Test {
public static native String hallbBase64(String str);
public static native String hellaBase64(String str);
public static native String hellbBase64(String str);
public static native String helloBaae64(String str);
public static native String helloBasa64(String str);
public static native String helloBase64(String str);
static {
System.loadLibrary("ooo");
System.loadLibrary("ooo111");
System.loadLibrary("ooo2222");
System.loadLibrary("ooo333");
}
}
复制这里应该是考察到底是哪个so对应着真正的方法,使用jnitrace 看一下
jnitrace -l libooo333.so -l libooo2222.so -l libooo111.so -l libooo.so com.zapata.r0zapatanative
ps: 跟github描述的不符合, 不能使用 -l *,否则会报错
输入内容 123456789
/* TID 930 */
5307 ms [+] JavaVM->GetEnv
5307 ms |- JavaVM* : 0x77a54cf500
5307 ms |- void** : 0x7fca40acb0
5307 ms |: 0x77a5445ea0
5307 ms |- jint : 65542
5307 ms |= jint : 0
5307 ms ------------------------------------Backtrace------------------------------------
5307 ms |-> 0x778910131c: _ZN7_JavaVM6GetEnvEPPvi+0x34 (libooo333.so:0x7789100000)
5307 ms |-> 0x778910131c: _ZN7_JavaVM6GetEnvEPPvi+0x34 (libooo333.so:0x7789100000)
/* TID 930 */
5311 ms [+] JNIEnv->FindClass
5311 ms |- JNIEnv* : 0x77a5445ea0
5311 ms |- char* : 0x77891014e8
5311 ms |: com/zapata/r0zapatanative/Test
5311 ms |= jclass : 0x81 { com/zapata/r0zapatanative/Test }
5311 ms -------------------------------------Backtrace-------------------------------------
5311 ms |-> 0x7789101354: _ZN7_JNIEnv9FindClassEPKc+0x2c (libooo333.so:0x7789100000)
5311 ms |-> 0x7789101354: _ZN7_JNIEnv9FindClassEPKc+0x2c (libooo333.so:0x7789100000)
复制从日志上看,锁定是libooo333.so
libooo333.so看看,最终会调用到一个base64_enc 的函数,改函数使用了一个byte_13A8 的数组.rodata:00000000000013A8 41 42 43 44 45 46 47 48 49 4A+aAbcdefghijklmn DCB "ABCDEFGHIJKLMNOPQRSTUVWXYZbacdefghijklmnopqrstuvwxyz0123456789+/"
.rodata:00000000000013A8 4B 4C 4D 4E 4F 50 51 52 53 54+ ; DATA XREF: base64_enc(char const*,char *)+10↑o
.rodata:00000000000013E8 FF unk_13E8 DCB 0xFF ; DATA XREF: base64_dec(char *,char *)+BC↑o
复制明显就是一个base64的字典
使用CyberChef , 输入反编译的那个验证字符串看看(字典设置为 ABCDEFGHIJKLMNOPQRSTUVWXYZbacdefghijklmnopqrstuvwxyz0123456789+/)
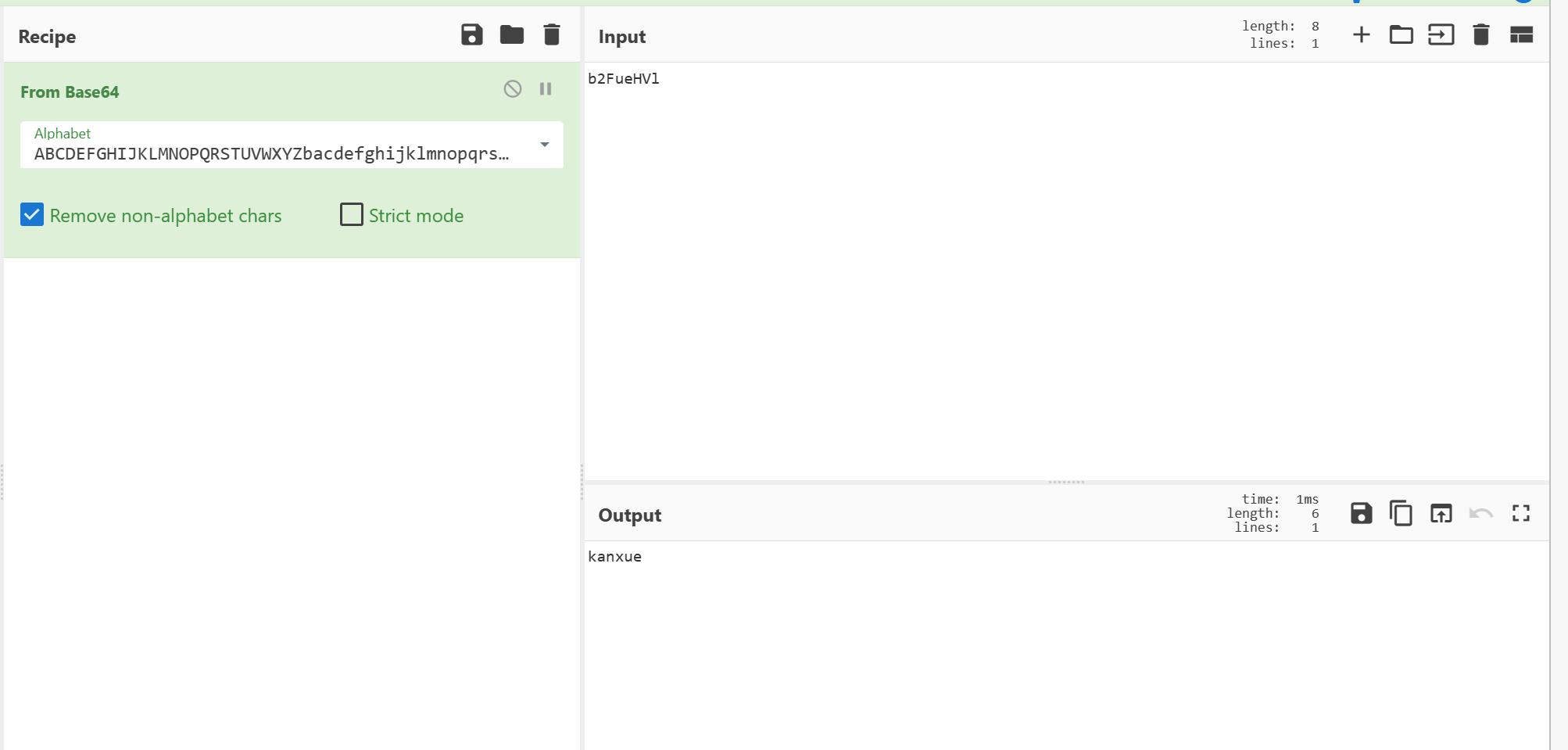
成功得到正确密码