抓取log
03-29 16:15:37.545 25910 26539 D KM-NATIVE: call Java_com_km_encryption_api_Security_sign
03-29 16:15:37.558 25910 26556 D KM-NATIVE: call Java_com_km_encryption_api_Security_sign
03-29 16:15:37.559 25910 26556 D KM-NATIVE: call Java_com_km_encryption_api_Security_sign
复制发现调取了这么个函数
var process_Obj_Module_Arr = Process.enumerateModules();
for(var i = 0; i < process_Obj_Module_Arr.length; i++) {
//包含"lib"字符串的
if(process_Obj_Module_Arr[i].path.indexOf("lib")!=-1)
{
//console.log("模块名称:",process_Obj_Module_Arr[i].name);
// console.log("模块地址:",process_Obj_Module_Arr[i].base);
// console.log("大小:",process_Obj_Module_Arr[i].size);
// console.log("文件系统路径",process_Obj_Module_Arr[i].path);
var libname = process_Obj_Module_Arr[i].name
frida_Module_import(libname)
}
}
function frida_Module_import(libname) {
Java.perform(function () {
const hooks = Module.load(libname);
var Imports = hooks.enumerateImports();
for(var i = 0; i < Imports.length; i++) {
if (Imports[i].name.indexOf('Java_com_km_encryption') != -1) {
console.log("模块名称:",libname);
//函数类型
console.log("type:",Imports[i].type);
//函数名称
console.log("name:",Imports[i].name);
//属于的模块
console.log("module:",Imports[i].module);
//函数地址
console.log("address:",Imports[i].address);
}
}
});
}
复制发现在libcommon-encryption.so中
顺着sign,一路往下看,发现有个地方启动了一个线程,并执行了checkSignUseApplicationPackageManager方法
for ( i = 0; i < v34; ++i )
{
GetMethodID = (jmethodID (*)(JNIEnv *, jclass, const char *, const char *))&v37[2 * i];
*(_BYTE *)GetMethodID = byte_1F620[(unsigned __int8)v35[i] >> 4];
v47 = v35[i];
*((_BYTE *)GetMethodID + 1) = byte_1F620[v47 & 0xF];
}
v37[2 * v34] = 0;
_android_log_print(3, "KM-NATIVE", "PackageManager>>>sign: %s", v37);
a1->functions->DeleteLocalRef((JNIEnv *)a1, v33);
var10 = strcmp(v38, "846BB6E12205A3245D1E78C934EDA27EA02D5BD5");
operator delete[](v38);
if ( var10 )
{
v48 = "sign_check_sha1_error";
LABEL_95:
throwException(a1, v48);
return 0;
}
return 1;
}
复制对应的汇编代码
.text:00009082 FD F7 FA EF BLX j__ZdaPv ; operator delete[](void *)
.text:00009082
.text:00009086 00 2C CMP R4, #0
.text:00009088 3F F4 B7 AE BEQ.W loc_8DFA
复制把这里的CMP R4, #0改为CMP R4, R4,这样下一行就可以顺利跳转
借助反汇编工具https://armconverter.com/
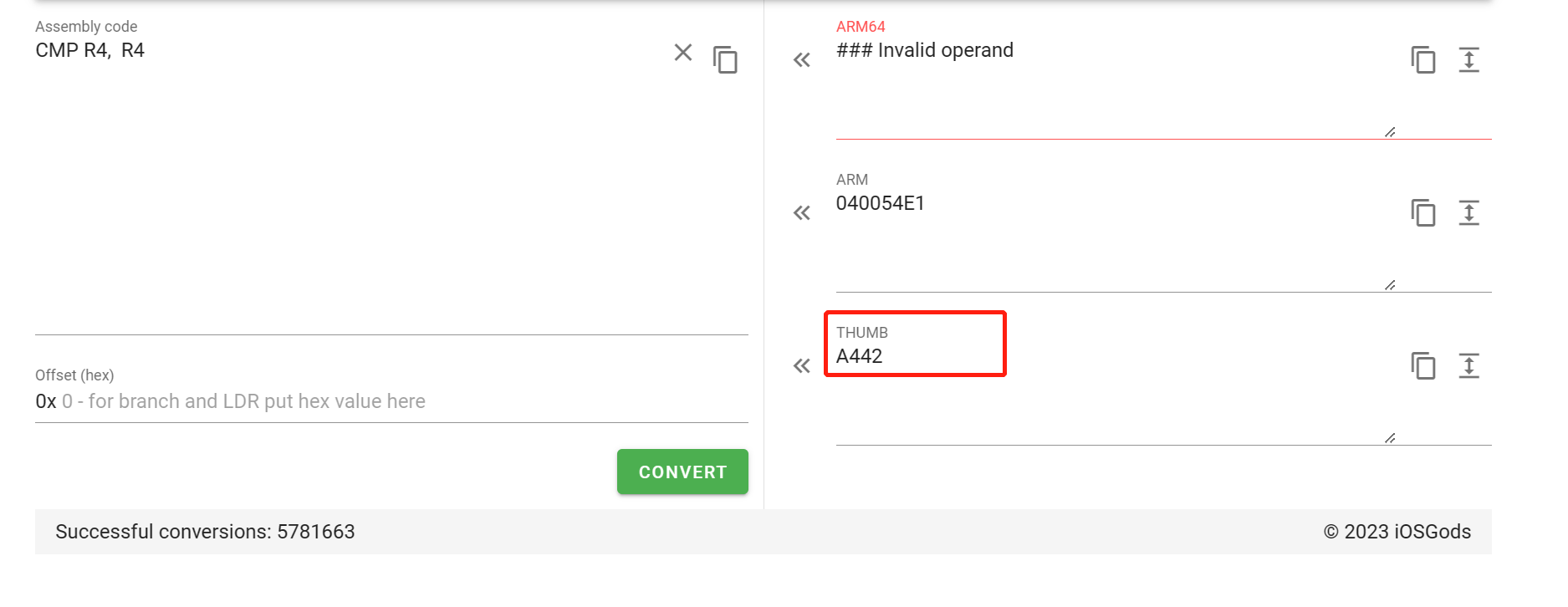
通过010Editor 把这里改为A442即可
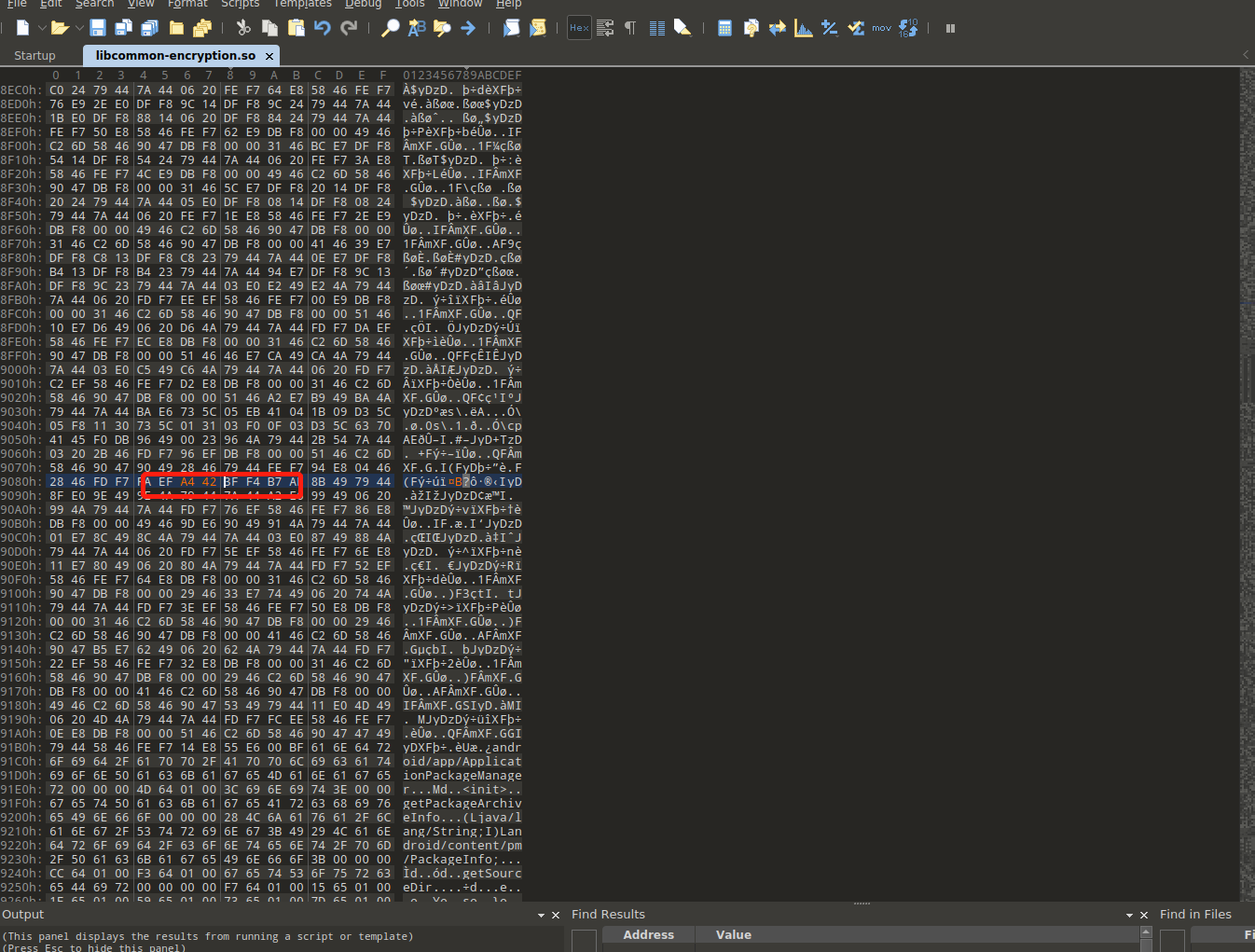 '
'
再次打开APP,运行正常功能正常,成功绕过签名校验