一、安装containerd
# yum install libseccomp -y
#下载containerd
curl -L https://github.com/containerd/containerd/releases/download/v1.6.0/cri-containerd-cni-1.6.0-linux-amd64.tar.gz -O cri-containerd-cni-1.6.0-linux-amd64.tar.gz
#解压containerd到根目录
tar zxvf cri-containerd-cni-1.6.0-linux-amd64.tar.gz -C /
#生成containerd配置
mkdir -p /etc/containerd
containerd config default > /etc/containerd/config.toml
#启动containerd
systemctl daemon-reload
systemctl enable containerd
systemctl start containerd
systemctl status containerd
#把cni命令ln到/usr/local/bin目录下
#ln -s /opt/cni/bin/* /usr/local/bin
curl -L https://github.com/opencontainers/runc/releases/download/v1.1.0/runc.amd64 -o /usr/local/sbin/runc
chmod +x /usr/local/sbin/runc
二、安装nerdctl
#下载nerdctl
curl -L https://github.com/containerd/nerdctl/releases/download/v0.18.0/nerdctl-0.18.0-linux-amd64.tar.gz -O nerdctl-0.18.0-linux-amd64.tar.gz
tar zxvf nerdctl-0.18.0-linux-amd64.tar.gz -C /usr/local/sbin
echo "alias docker='nerdctl --namespace k8s.io'" >> /etc/profile
echo "alias docker-compose='nerdctl compose'" >> /etc/profile
source /etc/profile
#配置nerdctl
mkdir -p /etc/nerdctl/
cat > /etc/nerdctl/nerdctl.toml << 'EOF'
namespace = "k8s.io"
insecure_registry = true
cni_path = "/data/kube/bin"
EOF
三、安装buildkit
#下载buildkit
curl -L https://github.com/moby/buildkit/releases/download/v0.9.3/buildkit-v0.9.3.linux-amd64.tar.gz -o buildkit-v0.9.3.linux-amd64.tar.gz
tar zxvf buildkit-v0.9.3.linux-amd64.tar.gz -C /usr/local/
#/etc/buildkit/buildkitd.toml为buildkitd默认配置
mkdir -p /etc/buildkit/
cat > /etc/buildkit/buildkitd.toml << 'EOF'
debug = true
root is where all buildkit state is stored.
root = "/var/lib/buildkit"
insecure-entitlements allows insecure entitlements, disabled by default.
insecure-entitlements = [ "network.host", "security.insecure" ]
[worker.oci]
enabled = true
platforms = [ "linux/amd64", "linux/arm64" ]
snapshotter = "auto"
rootless = false
noProcessSandbox = false
gc = true
gckeepstorage = 9000
max-parallelism = 4
[[worker.oci.gcpolicy]]
keepBytes = 512000000
keepDuration = 172800
filters = [ "typesource.local", "typeexec.cachemount", "type==source.git.checkout"]
[registry."19.15.14.158:31104"]
mirrors = ["19.15.14.158:31104"]
http = true #使用http协议
insecure = true #不验证安全证书
[registry."mmzwwwdocker.xxxxxx.com:31104"]
mirrors = ["mmzwwwdocker.xxxxxxx.com:31104"]
http = true #使用http协议
insecure = true #不验证安全证书
EOF
cat > /etc/systemd/system/buildkit.service << 'EOF'
[Unit]
Description=BuildKit
Documentation=https://github.com/moby/buildkit
[Service]
ExecStart=/usr/local/bin/buildkitd --oci-worker=false --containerd-worker=true
[Install]
WantedBy=multi-user.target
EOF
systemctl daemon-reload
systemctl enable buildkit
systemctl start buildkit
systemctl status buildkit
四、测试
mkdir test
cd test
cat > Dockerfile << 'EOF'
FROM alpine
EOF
docker build --platform arm64,amd64 -t test1 .
[+] Building 4.6s (7/7) FINISHED
=> [internal] load build definition from Dockerfile 0.0s
=> => transferring dockerfile: 49B 0.0s
=> [internal] load .dockerignore 0.0s
=> => transferring context: 2B 0.0s
=> [linux/amd64 internal] load metadata for docker.io/library/alpine:latest 0.6s
=> [linux/arm64 internal] load metadata for docker.io/library/alpine:latest 2.6s
=> CACHED [linux/amd64 1/1] FROM docker.io/library/alpine@sha256:21a3deaa0d32a8057914f36584b5288d2e5ecc984380bc0118285c70fa8c9300 0.0s
=> => resolve docker.io/library/alpine@sha256:21a3deaa0d32a8057914f36584b5288d2e5ecc984380bc0118285c70fa8c9300 0.0s
=> [linux/arm64 1/1] FROM docker.io/library/alpine@sha256:21a3deaa0d32a8057914f36584b5288d2e5ecc984380bc0118285c70fa8c9300 1.7s
=> => resolve docker.io/library/alpine@sha256:21a3deaa0d32a8057914f36584b5288d2e5ecc984380bc0118285c70fa8c9300 0.0s
=> => sha256:9b3977197b4f2147bdd31e1271f811319dcd5c2fc595f14e81f5351ab6275b99 2.10MB / 2.72MB 1.9s
=> exporting to oci image format 1.9s
=> => exporting layers 0.0s
=> => exporting manifest sha256:1bfa860f8991c3b6952fbb59493e8c346c4e46a78fff4099b4d95d87ad741283 0.0s
=> => exporting config sha256:69d06718b798aebf8c13b1a53299d1f791f8118dcd0fa9a0a827bf2f595aa9ca 0.0s
=> => exporting manifest sha256:e3b23b57855e132673409165a5a6559180c32d273399f13cf078163fea7398a0 0.0s
=> => exporting config sha256:35e223a20dbce8c0b81d3257f8cad0c7b2b35d8e18eadfec7eeb7de86a472e7b 0.0s
=> => exporting manifest list sha256:631ae1b627eb47a92dbaa80d1f2f4d38bd0b2b9196736076053e02689a27101c 0.0s
=> => sending tarball 0.1s
unpacking docker.io/library/test1:latest (sha256:631ae1b627eb47a92dbaa80d1f2f4d38bd0b2b9196736076053e02689a27101c)...done

测试动行时
docker run -d -p 80:80 nginx
iptables -t nat -nvL

五、配置私有仓库
vim /etc/containerd/config.toml
[plugins."io.containerd.grpc.v1.cri".registry]
config_path = ""
<span class="token punctuation">[</span>plugins.<span class="token string">"io.containerd.grpc.v1.cri"</span>.registry.auths<span class="token punctuation">]</span>
<span class="token punctuation">[</span>plugins.<span class="token string">"io.containerd.grpc.v1.cri"</span>.registry.auths.<span class="token string">"harbor.kids.com"</span><span class="token punctuation">]</span>
username <span class="token operator">=</span> <span class="token string">"admin"</span>
password <span class="token operator">=</span> <span class="token string">"Harbor123456"</span>
<span class="token punctuation">[</span>plugins.<span class="token string">"io.containerd.grpc.v1.cri"</span>.registry.configs<span class="token punctuation">]</span>
<span class="token punctuation">[</span>plugins.<span class="token string">"io.containerd.grpc.v1.cri"</span>.registry.configs.<span class="token string">"harbor.kids.com"</span>.tls<span class="token punctuation">]</span>
insecure_skip_verify <span class="token operator">=</span> <span class="token boolean">true</span>
<span class="token punctuation">[</span>plugins.<span class="token string">"io.containerd.grpc.v1.cri"</span>.registry.headers<span class="token punctuation">]</span>
<span class="token punctuation">[</span>plugins.<span class="token string">"io.containerd.grpc.v1.cri"</span>.registry.mirrors<span class="token punctuation">]</span>
<span class="token punctuation">[</span>plugins.<span class="token string">"io.containerd.grpc.v1.cri"</span>.registry.mirrors.<span class="token string">"docker.io"</span><span class="token punctuation">]</span>
endpoint <span class="token operator">=</span> <span class="token punctuation">[</span><span class="token string">"https://registry-1.docker.io"</span><span class="token punctuation">]</span>
<span class="token punctuation">[</span>plugins.<span class="token string">"io.containerd.grpc.v1.cri"</span>.registry.mirrors.<span class="token string">"harbor.kids.com"</span><span class="token punctuation">]</span>
endpoint <span class="token operator">=</span> <span class="token punctuation">[</span><span class="token string">"https://harbor.kids.com"</span><span class="token punctuation">]</span> <span class="token comment">#如果是http时,改为http</span>
<span class="token punctuation">[</span>plugins.<span class="token string">"io.containerd.grpc.v1.cri"</span>.registry.tlss<span class="token punctuation">]</span>
<span class="token punctuation">[</span>plugins.<span class="token string">"io.containerd.grpc.v1.cri"</span>.registry.tlss.<span class="token string">"harbor.kids.com"</span><span class="token punctuation">]</span>
ca_file <span class="token operator">=</span> <span class="token string">"/home/data/cert/ca.pem"</span>
cert_file <span class="token operator">=</span> <span class="token string">"/home/data/cert/harbor.pem"</span>
key_file <span class="token operator">=</span> <span class="token string">"/home/data/cert/harbor-key.pem"</span>
复制
六、nerdctl 使用http 的harbor
nerdctl login harbor.cadp.com --insecure-registry -u admin -p Harbor123456
WARN[0000] WARNING! Using --password via the CLI is insecure. Use --password-stdin.
WARN[0000] skipping verifying HTTPS certs for "harbor.cadp.com"
WARNING: Your password will be stored unencrypted in /root/.docker/config.json.
Configure a credential helper to remove this warning. See
https://docs.docker.com/engine/reference/commandline/login/#credentials-store
Login Succeeded
#拉取镜像
docker pull harbor.cadp.com/smartgate/gwit:v5 --insecure-registry
#这个为ctr 下载镜像命令
ctr -n k8s.io i pull --plain-http harbor.cadp.com/smartgate/gwit:v5
# --plain-http 表示使用http下载
#推送镜像
docker push harbor.cadp.com/public/elasticsearch:7.13.1 --insecure-registry
https://kubernetes-release.pek3b.qingstor.com/containerd/containerd/releases/download/v1.6.4/containerd-1.6.4-linux-amd64.tar.gz
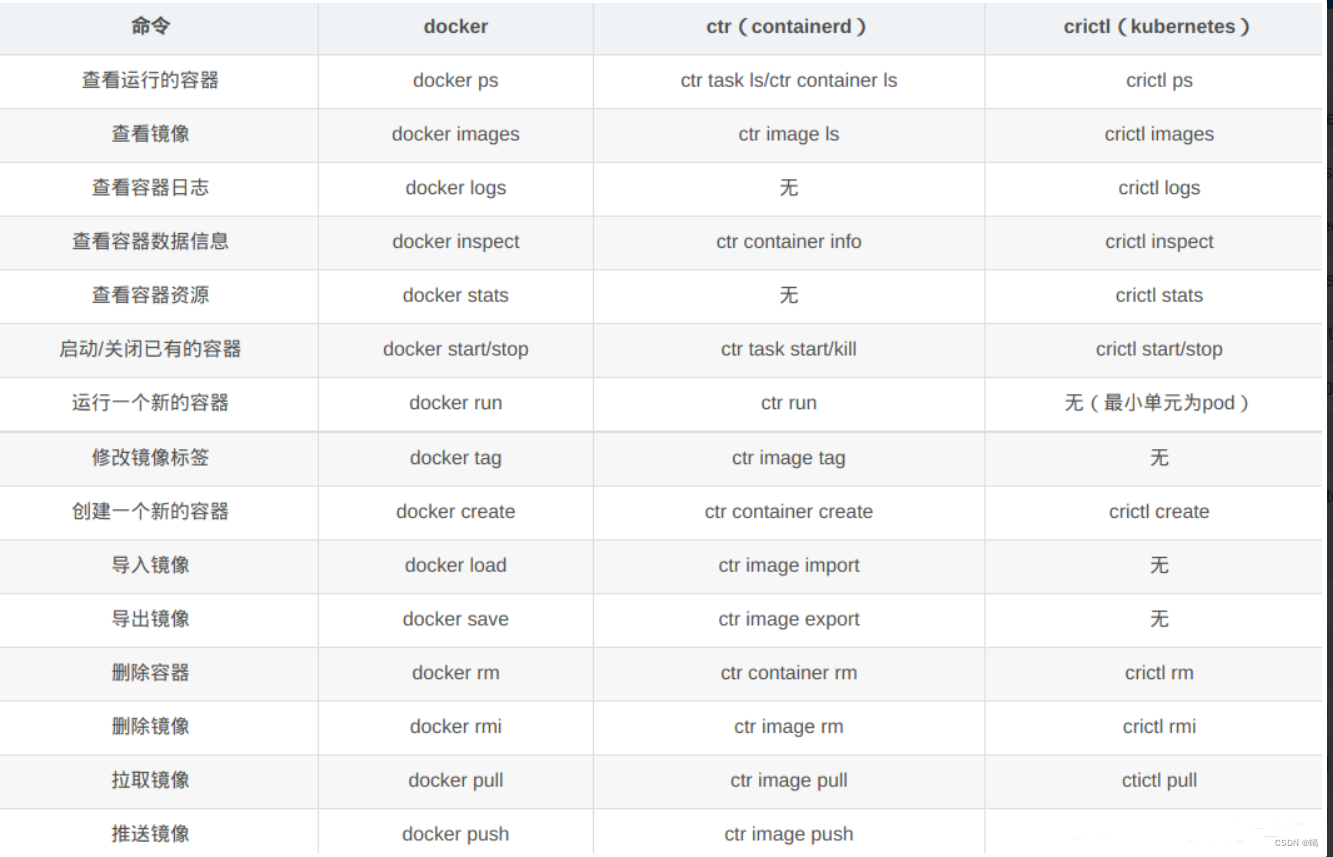
- nerdctl docker ctr命令